IBM Cloud™ Docker Registry - Push and Scan for Common Vulnerabilities, and Exposures (CVE)
IBM Cloud™ scans images in their Docker Container Registry (DCR)
Introduction
Vulnerability Advisor provides security management for IBM Cloud™ Container Registry, generating a security status report that includes suggested fixes and best practices.
When you add an image to a namespace, the image is automatically scanned by Vulnerability Advisor to detect security issues and potential vulnerabilities. If security issues are found, instructions are provided to help fix the reported vulnerability.
Any issues that are found by Vulnerability Advisor result in a verdict that indicates that it is not advisable to deploy this image. If you choose to deploy the image, any containers that are deployed from the image include known issues that might be used to attack or otherwise compromise the container. The verdict is adjusted based on any exemptions that you specified. This verdict can be used by Container Image Security Enforcement to prevent the deployment of nonsecure images in IBM Cloud™ Kubernetes Service (IKS).
Fixing the security and configuration issues that are reported by Vulnerability Advisor can help you to secure your XtremeCloud Applications that are deployed to IKS.
Tag, Push, and Analyze the Results
Let’s tag and push our brand provider Docker Image to the IBM Cloud™ Container Registry:
[centos@vm-controller xtremecloud-brand]$ docker tag registry.gitlab.com/eupraxialabs/xtremecloud-brand:3.1.2 us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2
[centos@vm-controller xtremecloud-brand]$ docker push us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2
The push refers to a repository [us.icr.io/eupraxialabs/xtremecloud-brand]
b8c352029964: Pushed
f435434daeec: Pushed
b3920d5c9c89: Pushed
37a63b5c958f: Pushed
408dd085e29a: Pushed
d9ff549177a9: Pushed
3.1.2: digest: sha256:00c16c4ad0d2e3ec7398a35ce67cc73d074467638ff74641bdeece39b106aa28 size: 1588
[centos@vm-controller xtremecloud-brand]$ ibmcloud cr image-list
Listing images...
REPOSITORY TAG DIGEST NAMESPACE CREATED SIZE SECURITY STATUS
us.icr.io/eupraxialabs/xtremecloud-brand 3.1.2 00c16c4ad0d2 eupraxialabs 3 days ago 85 MB Scanning...
OK
[centos@vm-controller xtremecloud-brand]$ ibmcloud cr image-list
Listing images...
REPOSITORY TAG DIGEST NAMESPACE CREATED SIZE SECURITY STATUS
us.icr.io/eupraxialabs/xtremecloud-brand 3.1.2 00c16c4ad0d2 eupraxialabs 3 days ago 85 MB 1 Issue
OK
Now, let’s look at a vulnerability assessment:
[centos@vm-controller xtremecloud-brand]$ ibmcloud cr va us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2
Checking security issues for 'us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2'...
Image 'us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2' was last scanned on Tue Nov 5 19:20:11 UTC 2019
The scan results show that 1 ISSUE was found for the image.
Vulnerable Packages Found
=========================
Vulnerability ID Policy Status Affected Packages How to Resolve
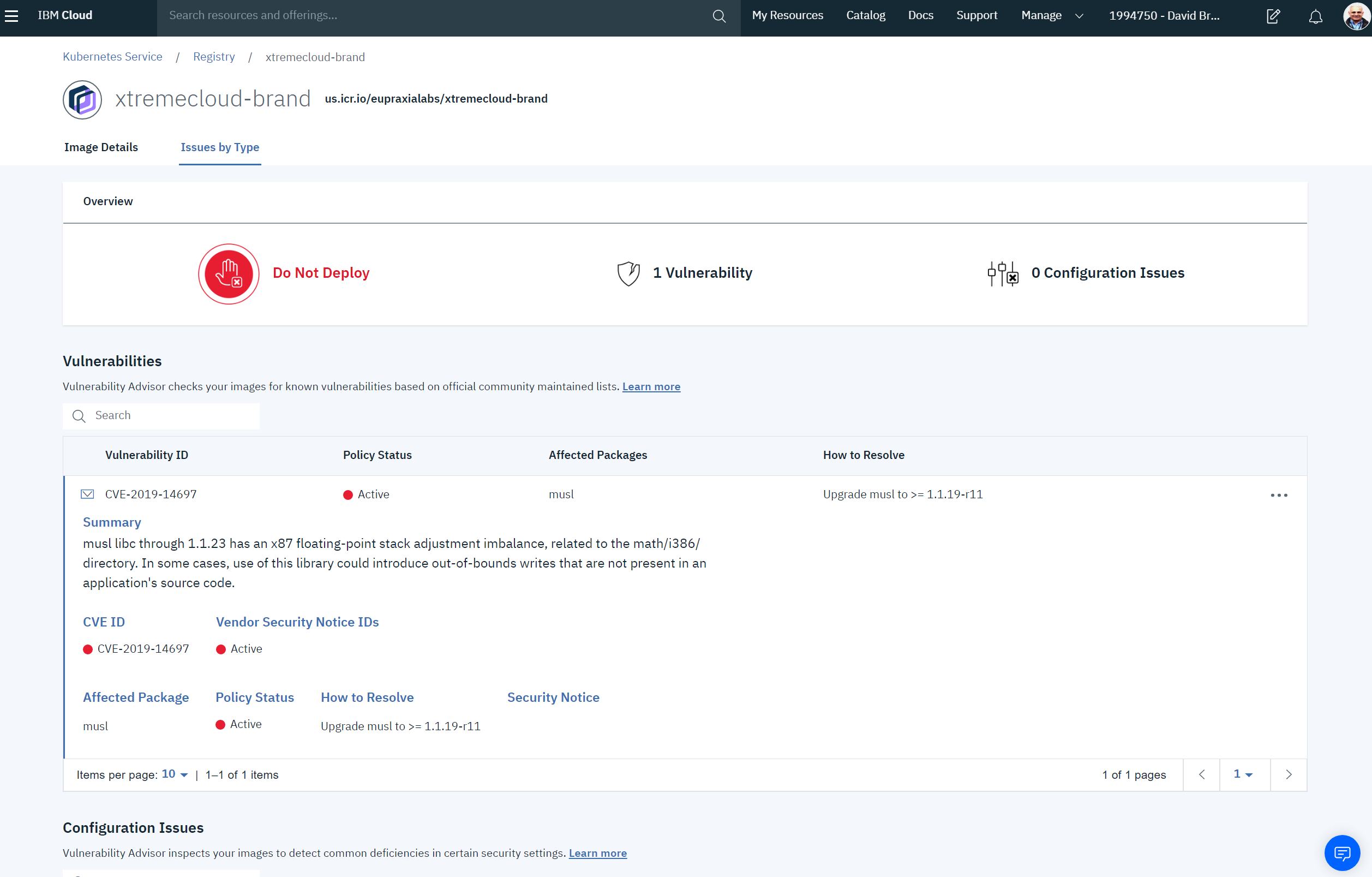
CVE-2019-14697 Active musl Upgrade musl to >= 1.1.19-r11
To see the details about the fixes for these packages, run the command again with the '--extended' flag.
OK
So, let’s look at the extended information that is provided at the command line:
[centos@vm-controller xtremecloud-brand]$ ibmcloud cr va us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2 --extended
Checking security issues for 'us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2'...
Image 'us.icr.io/eupraxialabs/xtremecloud-brand:3.1.2' was last scanned on Tue Nov 5 19:20:11 UTC 2019
The scan results show that 1 ISSUE was found for the image.
Vulnerable Packages Found
=========================
CVE-2019-14697
Policy Status
Active
Summary
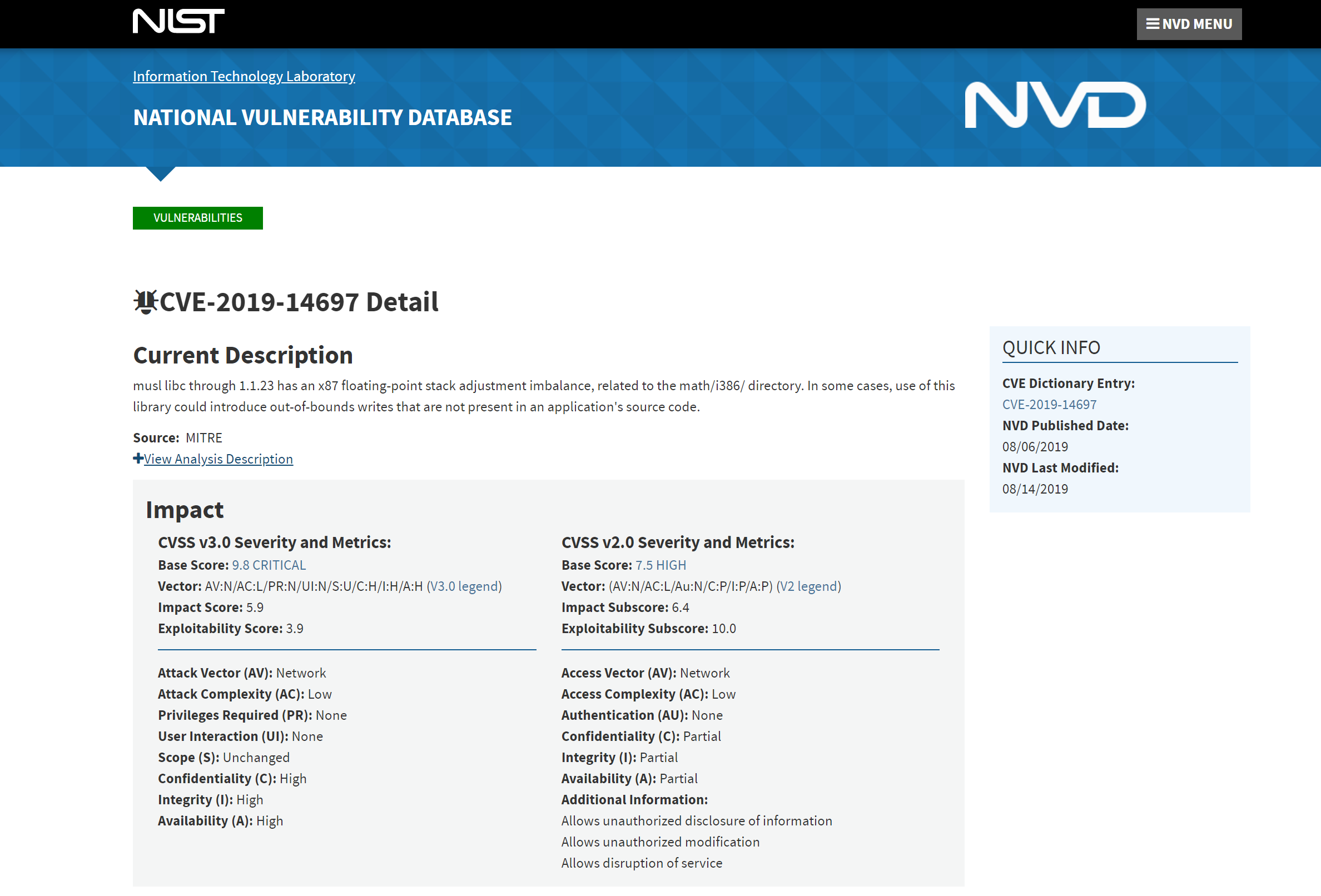
musl libc through 1.1.23 has an x87 floating-point stack adjustment imbalance, related to the math/i386/ directory. In some cases, use of this library could introduce out-of-bounds writes that are not present in an application's source code.
Vendor Security Notice IDs Official Notice
ALPINE-CVE-2019-14697
Affected Packages Policy Status How to Resolve Security Notice
musl Active Upgrade musl to >= 1.1.19-r11 ALPINE-CVE-2019-14697
OK
Let’s look up the CVE at the NIST National Vulnerability Database:
If you prefer to use the IBM Cloud™ browser user interface, the CVE can be reviewed in this manner: